Intro
In the ever-evolving landscape of remote work, where the boundaries between office and home blur, a new realm of challenges has emerged – cybersecurity risks that cast a shadow over the digital workspace.
As we delve into the heart of this virtual paradigm, a tapestry of statistics unveils the multifaceted nature of these risks. From the surge of phishing attacks to the ominous allure of ransomware, the vulnerability of unsecured Wi-Fi networks, and the unseen menace of inadequate endpoint security – each statistic tells a tale of vigilance and caution.

Stats
A study published showing remote work boosts risk showed that 2020 saw a 400% surge in cyberattacks, hitting home networks hard. Unsecured devices, weak passwords, and lapses in training opened doors to breaches. 72% of firms reported remote-related security incidents.
If we talk about the recent data of 2023, according to one research, 72% of respondents reported worries related to cybersecurity. Which again raises concern about this global problem.
Yet, hope blooms: $1 trillion is set to shield us by 2025. So, by staying watchful, using MFA, and learning more about Cybersecurity can work well for all of us. As this is the only our armor against digital threats.
What Are Cybersecurity Risks?
Imagine your digital life as a puzzle, each piece representing your personal info, business secrets, and more. Cyber threats are like sneaky thieves trying to steal, mess up, or break those pieces.

The All-in-One Platform for Effective SEO
Behind every successful business is a strong SEO campaign. But with countless optimization tools and techniques out there to choose from, it can be hard to know where to start. Well, fear no more, cause I've got just the thing to help. Presenting the Ranktracker all-in-one platform for effective SEO
We have finally opened registration to Ranktracker absolutely free!
Create a free accountOr Sign in using your credentials
Cybercriminals employ various tactics, such as fraud emails, ransomware like WannaCry, and even power disruptions like Stuxnet. In this ever-evolving digital landscape, safeguarding your digital assets is paramount.
Your online security is akin to a delicate puzzle; handle it with care. It is advised to practice discretion when sharing information, trust reputable sources, and regularly update your software.
It's imperative to prepare for potential cyberattacks by having a well-thought-out plan for recovery. Traverse this digital terrain thoughtfully; your digital pieces are invaluable. Stay vigilant and stay secure!
Are They Life-Threatening?
Remote work's cyber risks, while not immediately life-threatening, carry serious personal and professional consequences. Data breaches jeopardize finances and privacy, causing shivers at the thought of unauthorized access.

Ransomware acts like a digital bully, holding files hostage and disrupting routines. Weak passwords leave us vulnerable, like an open front door. Insider attacks, third-party breaches, and infrastructure weaknesses extend harm beyond individuals. While not fatal, these risks demand vigilance, strong passwords, updates, encryption, training, and data backups for protection in our increasingly digital lives.
Security Concerns
Cybersecurity safeguards computer systems, networks, software, and data from threats and unauthorized access. Evolving with technology, concerns include data breaches, malware attacks, camera’s getting hacked, ransomware, insider threats, IoT vulnerabilities, website hacks, and more.

The All-in-One Platform for Effective SEO
Behind every successful business is a strong SEO campaign. But with countless optimization tools and techniques out there to choose from, it can be hard to know where to start. Well, fear no more, cause I've got just the thing to help. Presenting the Ranktracker all-in-one platform for effective SEO
We have finally opened registration to Ranktracker absolutely free!
Create a free accountOr Sign in using your credentials
Zero-day vulnerabilities, social engineering, and inadequate security awareness pose risks. To overcome these situations, firewalls, patch management, and guarding against supply chain attacks and cloud vulnerabilities are vital.
By employing technical measures, protocols, training, and vigilance, individuals and organizations can effectively counter these concerns in the dynamic cybersecurity landscape.
How Cybersecurity Risks Affects Hybrid Work Culture?
The rise of hybrid work, blending remote and in-office presence, brings a balance between productivity and personal life. However, it also introduces cybersecurity risks.

Picture working from home, an HR email prompts you to click for benefits update. It's phishing, compromising data.
Hybrid work can lower guards against credit card hacking, using AI in the wrong way to attack people online. Meanwhile, at the office, a phone update via USB introduces malware, jeopardizing data. Personal devices pose malware risks. Weak home Wi-Fi passwords invite hackers, breaching data.
To tackle such situations, secure remote connections with VPNs and encryption are crucial. Hybrid work demands robust cybersecurity, prioritizing education, protocols, and tools.
Use project management tools like Airtable, to create a secure workflow within the organization. If you run an automobile blog or any other niche, there are so many confidential document that using these tools increases productivity, and every information you share is secured.
The best suggestion while choosing similar tools is to look at your team size, cost-effectiveness, time-saving, and security.
Is Artificial Intelligence A Threat To Organisation?
Artificial intelligence (AI) has the power to completely change industries and spur innovation. However, it poses serious difficulties. Automation-related job loss is a serious worry, particularly in industries like retail where AI-driven systems take the place of human employees. Reskilling the workforce is essential to ensuring workforce adaptation.

- Particularly in the healthcare industry, where AI can access sensitive patient data, privacy and data security are of utmost importance. Strong confidentiality safeguards are essential to protect this information.
- As AI makes quick decisions, such as driverless vehicles putting safety first, ethical quandaries arise. A balanced integration requires ethical AI development, upskilling, diligent data management, and harmonious human-AI collaboration.
- A commitment to building a positive AI-driven future underpins the journey ahead, which involves technological improvements, ethical concerns, workforce development, and appropriate data management.
Cyber Security Risks For Small Businesses Involved With AI?
Cybersecurity risks for small businesses with the use of AI create concerns about insider threats. Employees could unintentionally or intentionally exploit AI systems, thereby exposing confidential information.
AI systems' interconnection increases the attack surface, making it simpler for hackers to find your weaknesses and get access to vital systems. The staff may be tricked by AI-driven phishing assaults, and depending on external AI providers exposes them to supply chain risks.
Small businesses can effectively mitigate cybersecurity risks by:
- Investing in staff training,
- Outsourcing to reliable cybersecurity experts,
- Performing routine security audits, and
- Staying up-to-date with the latest threats and regulations.
Top 5 Cybersecurity Risk Examples
Well, when you talk about Cyber risk, let us see the top 5 Cybersecurity risks that you may experience with examples to understand it better:
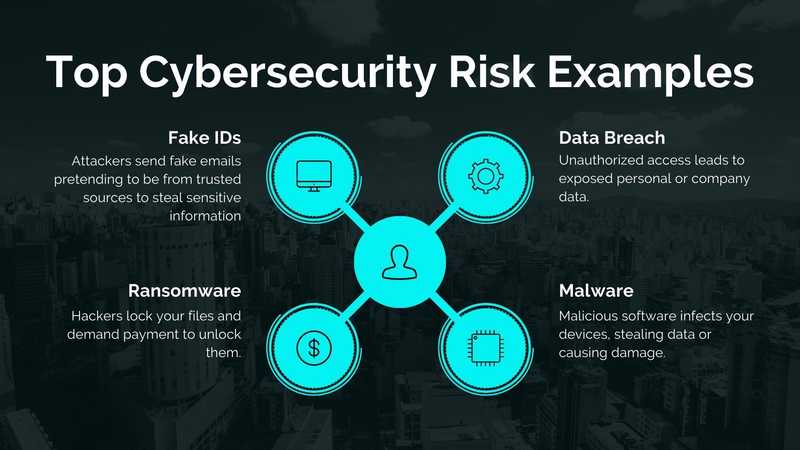
Fake IDs: Attackers send fake id emails pretending to be from trusted sources to steal sensitive information.
Example: You have opted for U-Haul roadside assistance, and some unknown attacker is calling to know about your information, such as your social security number, insurance ID, etc., to make a false claim.
Malware: Malicious software infects your devices, stealing data or causing damage.
Example: Downloading an attachment that secretly installs a virus on your computer.
Ransomware: Hackers lock your files and demand payment to unlock them.
Example: Your business's important files get encrypted, and you're asked to pay a ransom to access them.
Data Breach: Unauthorized access leads to exposed personal or company data.
Example: Hackers breaking into a company's database and leaking customer information.
Weak Passwords: Using simple, easy-to-guess passwords makes it easier for attackers to access accounts.
Example: Using "123456" as your password for multiple online accounts.
Expert Insights On Cybersecurity Risk
“I have seen people listing their items on Facebook, fooling people into becoming victims of a Facebook marketplace scam. The seller asks for payments in advance; all the listed item images are stock photos, priced at a low price like $999, and never sends the actual product.” People can save themselves from cyber risks and Facebook marketplace scams by knowing the red flags in a deal.
Er. Ankit Dhadwal, Founder & CEO of Mount Shine.
“The misuse of personal information by some individuals has become a major concern. Often, we are not even aware that our personal data is being used without our knowledge. However, Google's dark web report offers a solution to this problem. By entering your email address, the report shows the websites where your information is being used on the dark web. This is a great start to addressing the issue, and other companies should consider implementing similar measures.”
Gaurav Pundir, the Founder and CEO of OMGGamer.com
“A successful insider risk program focuses on the people, processes, and technologies. Managing both internal and external risks is vital to the security of any organization. Each comes with its own challenges, but what makes insider risk management especially tricky is the need to balance people, processes, and technologies.”
Bret Arsenault, Microsoft’s chief information security officer, said in an article published by Harvard Business Review.
How To Tackle Cybersecurity Risks?
Well, as we have discussed, the Cybersecurity risks and how they affect our day to lives. We all know how dangerous it can be for mankind. So, by considering all of this, we try to understand the possible solutions we can implement in our lives. We can save ourselves from the Cyber trap by including the following basic changes.
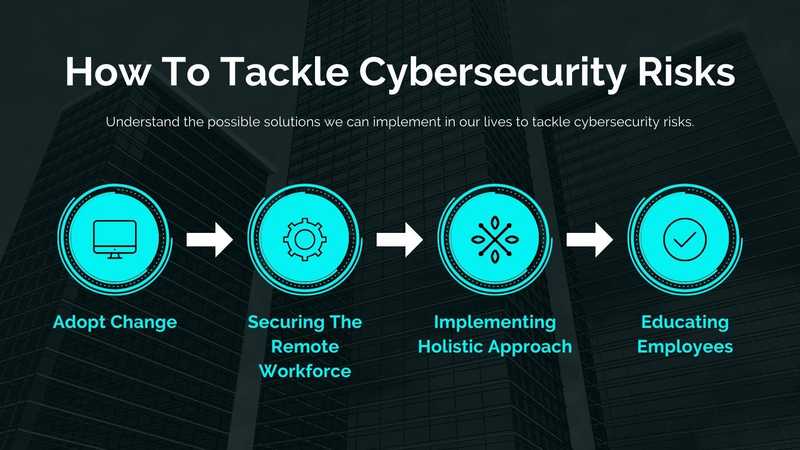
1. Adopt Change
In our digital era, cybersecurity is paramount. Be vigilant against cyber threats with steps like staying informed, strong passwords, and regular updates.
For instance,
- Using multi-factor authentication adds an extra layer of security.
- Safeguard networks through encryption;
- avoid public Wi-Fi like unsecured cafes.
- Be cautious of fake emails;
- verify the sender's authenticity.
- Regular data backups, like cloud storage, aid recovery from attacks.
- Employ trusted sources, firewalls;
- Limit personal info sharing.
- Train staff, develop incident response plans, and audit for vulnerabilities.
- Secure IoT devices, watch for social engineering and seek expert advice to fortify defenses.
2. Securing The Remote Workforce
Securing the remote workforce is paramount to evading cyber threats. With the rise in remote work, implementing robust cybersecurity measures is essential. Companies should enforce strong authentication, encrypt communication, and educate employees about cyber scams. Regular software updates and access controls help fortify defenses. Implementing a robust education cybersecurity solution is essential to safeguard sensitive information and ensure a secure learning environment for students and staff in educational institutions.
Organizations can create a safer digital environment and thwart potential cyber traps by fostering a culture of vigilance and providing remote employees with the necessary tools.
It may add extra cost to their budget, but it is better than getting a threat of ransom emails, data breaches, and privacy issues in the future.
Our research has already shown how cybersecurity concerns will rise and appropriate solutions will be implemented by 2025. Additionally, paying attention to an Attack Library and conducting Network Security Testing are essential components of a comprehensive cybersecurity strategy. By staying informed about the latest threats, assessing and mitigating risks proactively, and continuously improving security defenses, organizations can better protect the data, systems, and assets from cyber attacks.
3. Implementing Holistic Approach
A holistic cybersecurity approach is like fortifying your digital stronghold to protect valuable assets from cyber threats. Just as a castle safeguards its treasures, identify your digital crown jewels—like customer data. Strengthen defenses with multi-factor authentication (MFA), making unauthorized access challenging.
Encryption acts as an impervious shield, rendering data useless to attackers. Prepare for contingencies with an incident response plan akin to vigilant knights defending your realm. Collaborate with trusted allies by sharing threat intelligence. Adhere to cybersecurity standards, your digital code of chivalry.
4. Educating Employees
Employee education is pivotal in cybersecurity as it can be either a vulnerability or the initial line of defense. To enhance security:
- Comprehensive Training: Institute thorough security training, encompassing fundamental concepts, phishing awareness, robust password practices, and multi-factor authentication. From 8 digits, the advised password strength is already up to 16 digits.
- Data Handling: Educate employees on proper data management, BYOD policies, safe browsing habits, and the importance of software updates.
- Incident Reporting: Establish clear protocols for reporting security incidents, emphasizing both physical and remote work security.
- Continuous Learning: Provide ongoing education to keep employees updated on evolving cyber threats.
- Accountability and Recognition: Implement consequences for non-compliance and reward good cybersecurity practices. Leadership Involvement: Start cybersecurity education from the top down to set the example.
- Regular Assessment: Conduct regular knowledge assessments to gauge employees' understanding.
5. Using AI For Cyber Defence
Each coin has two sides, and so does AI. Many companies are using AI to save people and vice-versa.
AI improves cyber defense by keeping an eye out for attacks, spotting vulnerabilities, and taking immediate action. It recognizes phishing emails and websites, stops malware, checks for vulnerabilities, and detects behavioral irregularities.
AI facilitates forensics, automates incident response, and adapts authentication. It enhances antivirus software and powers cutting-edge firewalls while processing data for insights.
Sharing threat intelligence is important, as is ongoing monitoring, data protection, and training. With employee training, access limits, encryption, and a solid response plan as part of a complete strategy, AI keeps cybersecurity vigilant against emerging threats.
5 Common Practises To Be Follow By Remote Employees
By following simple common practices, employees can protect themselves from cyber-attacks. They don’t need any expert advice on this case either. Here’s what they need to do:

- Use Multi-factor authentication for emails and wherever they sign up.
- Keep Devices Up To Date and go to authorized dealers only for updating devices.
- Deploy Anti-Malware Software that is licensed. Using pirated or cracked versions leads to more cyber threats.
- Protect Data by not sharing passwords, PINs, and so on.
- Sharing knowledge with others to create a protected environment.
Can Crisis Management Plans Help In Cybersecurity Risks?
Cybersecurity is becoming more important than ever in today's hyper-connected environment. Convenience and innovation are provided by the digital era, but it also brings continual cyber risks, such as hacking and data breaches. Plans for cybersecurity crisis management are essential to fend off these threats.

By combining preventative measures like strong security standards with quick responses, they serve as a safety net, guiding enterprises through the pandemonium of cyberattacks. Small or large, no organization is immune; all must prioritize these measures to secure their future in our technologically dependent society.
Future Of Hybrid WorkPlace
The hybrid workplace offers exciting opportunities but presents significant cybersecurity risks.

“Imagine your cozy home office with smart devices vulnerable to hackers. Phishing attacks have evolved, making you susceptible to scams even while communicating virtually. Public Wi-Fi at a coffee shop poses data theft risks without a VPN. Cloud storage and BYOD can lead to accidental data leaks, and insider threats are amplified.”
Prioritizing cybersecurity awareness and proactive measures is crucial for a secure hybrid work future. We humans have tackled many severe cases, and we’ll be making a better future for the hybrid workplace that will be secure and safe.
Conclusion
In today's dynamic era of remote work, cybersecurity is paramount. With technology constantly evolving and the lines between physical and virtual realities blurring, a holistic cybersecurity approach is vital. As we rely more on technology, we must recognize its vulnerabilities to increasingly sophisticated cyber threats.
Staying informed about threats, implementing security best practices, and fostering a culture of cybersecurity awareness are essential. Cybersecurity isn't a peripheral concern but our armor against digital threats. In this ever-changing landscape, we must protect our digital future and assets.
Let us know about your experiences and concerns with cybersecurity risks by tagging us in your social media posts. We’ll be happy to hear from you.
FAQs
Frequently Asked Questions about Cybersecurity Risks
Cybersecurity risks that 5G technology may face?
As the number of connected devices and IoT proliferation increase, cybercriminals have a larger attack surface, with each device being a potential entry point.
What is one of the greatest workplace cybersecurity risks when thinking about credential theft?
Credential theft is one of the greatest workplace cybersecurity risks that is one of the biggest concerns. Attackers act as conman who acts as your friend but takes all the details and misuses them.
The All-in-One Platform for Effective SEO
Behind every successful business is a strong SEO campaign. But with countless optimization tools and techniques out there to choose from, it can be hard to know where to start. Well, fear no more, cause I've got just the thing to help. Presenting the Ranktracker all-in-one platform for effective SEO
We have finally opened registration to Ranktracker absolutely free!
Create a free accountOr Sign in using your credentials
What kind of cybersecurity risks can be minimized by using a virtual private network (VPN)?
DDoS attacks, website hacking, and secure browsing are a few that can be minimized by using a virtual private network(VPN).
How to mitigate cybersecurity risks?
By making people aware of cybersecurity Insurance, conducting regular audits and assessments, board and executive involvement, and spreading a security awareness culture.